The phrase “inurl admin login PHP” is commonly associated with cyber security risks and highlights a recurring theme in internet usage: vulnerabilities in web application security. In this article, we will explore what the query means, its implications, the risks associated with insecure admin login portals, and best practices for safeguarding these entry points.
Table of Contents
ToggleWhat Does “inurl admin login PHP” Mean?
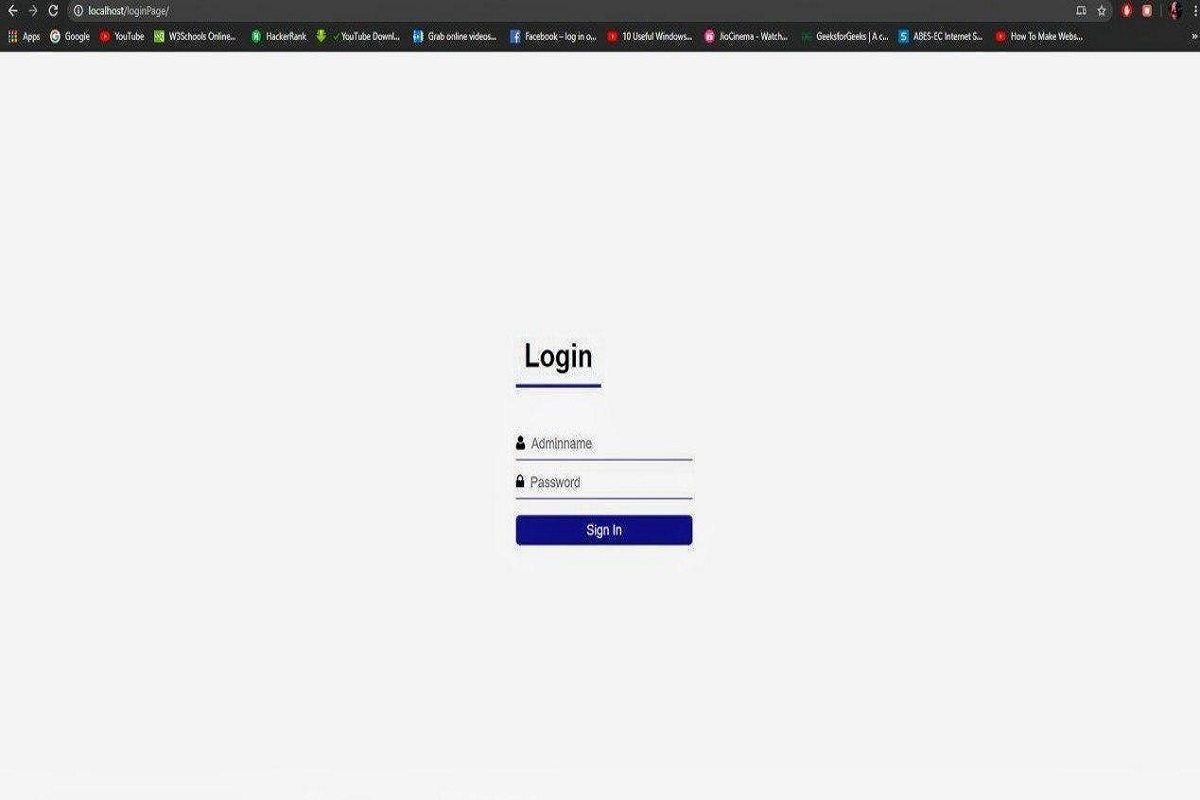
The term “inurl admin login PHP” is a search engine query designed to find web pages with “admin login” in their URLs. Particularly those written in PHP, a popular scripting language for developing web applications. It is often used by web administrators to locate admin login pages for management purposes. However, the same query can also attract malicious actors seeking to exploit poorly secured admin portals.
PHP, as one of the most widely used programming languages for building dynamic websites, powers millions of admin interfaces globally. These interfaces allow website administrators to manage their content, user data, and other backend functionalities. Unfortunately, unsecured or outdated admin portals can become a gateway for cyberattacks.
The Risks of Exposed Admin Portals
When admin login pages are easily discoverable through search engines, they expose businesses and websites to several risks. Below are the most prominent threats:
1. Brute Force Attacks
Hackers can use automated tools to attempt countless username and password combinations on exposed login pages. Without proper rate-limiting or CAPTCHA systems in place, a brute force attack can easily compromise such portals.
2. SQL Injection
Poorly developed login pages that do not sanitize user inputs can be vulnerable to SQL injection attacks. By injecting malicious SQL queries into the login fields, attackers can gain unauthorized access to databases, potentially stealing sensitive data or corrupting information.
3. Credential Theft
Some admin pages lack proper encryption during login processes, exposing user credentials to interception by man-in-the-middle attacks. This is especially risky for pages without HTTPS encryption.
4. Directory Traversal and File Inclusion
Hackers might use vulnerabilities in the PHP code to gain access to directories and files outside the intended web application scope, potentially retrieving sensitive information or uploading malicious scripts.
5. Denial of Service (DoS) Attacks
An easily accessible admin login page can also be the target of DoS attacks, where attackers flood the page with fake requests, making it inaccessible to legitimate users.
Preventing Exploitation of Admin Login Pages
While exposing admin login pages to the internet is often necessary for accessibility, ensuring they are secure should be a top priority. Below are several practices that website administrators should implement:
1. Restrict Access to Admin Pages
One of the simplest ways to secure admin pages is by limiting access based on IP addresses or using VPNs. This ensures that only authorized personnel can view or interact with the login page.
2. Implement Strong Authentication
Enable multi-factor authentication (MFA) to add an additional layer of security. Even if credentials are compromised, MFA can prevent unauthorized access.
3. Use Strong Password Policies
Enforce strong password policies for admin accounts, including the use of uppercase letters, numbers, symbols, and a minimum length of 12 characters. Additionally, encourage regular password changes.
4. Obfuscate Admin URLs
Avoid using predictable admin page URLs like /admin or /login.php. Instead, customize these paths to make them harder for attackers to locate through automated queries.
5. Secure the PHP Code
Ensure that all PHP scripts are secure by validating and sanitizing user inputs, using prepared statements for database interactions, and keeping PHP versions updated.
6. Enable HTTPS Encryption
Secure communication between users and the server by implementing HTTPS. This ensures that login credentials are encrypted and less susceptible to interception.
7. Deploy Web Application Firewalls (WAFs)
WAFs can filter and monitor HTTP traffic to and from a web application, blocking malicious activities before they reach the admin page.
Ethical Considerations and the Role of Search Engines
Search engines play a significant role in indexing web pages, including admin portals. While “inurl admin login PHP” may seem like a harmless query, its misuse highlights the ethical dilemma of open access to information. Search engines like Google actively combat malicious use by implementing safeguards and encouraging website owners to secure sensitive pages through measures like robots.txt files and the use of the “noindex” directive.
Web administrators are also responsible for not exposing sensitive URLs. Conducting regular audits and penetration tests can help identify vulnerabilities before they are exploited.
Conclusion
The “inurl admin login PHP” query underscores the dual-edged nature of the internet. While it serves as a useful tool for administrators, it also highlights the need for vigilance in web security. As cyber threats grow in sophistication, website owners and developers must adopt proactive measures to secure admin portals. By following best practices such as restricting access, implementing strong authentication, and keeping software up-to-date, organizations can significantly reduce their risk of compromise. In the digital age, a secure admin login page is not just a necessity—it is a responsibility.